Configuring Vaultwarden docker on CyberPanel
1. Pull docker images/cyberpanel/vaultwarden_docker
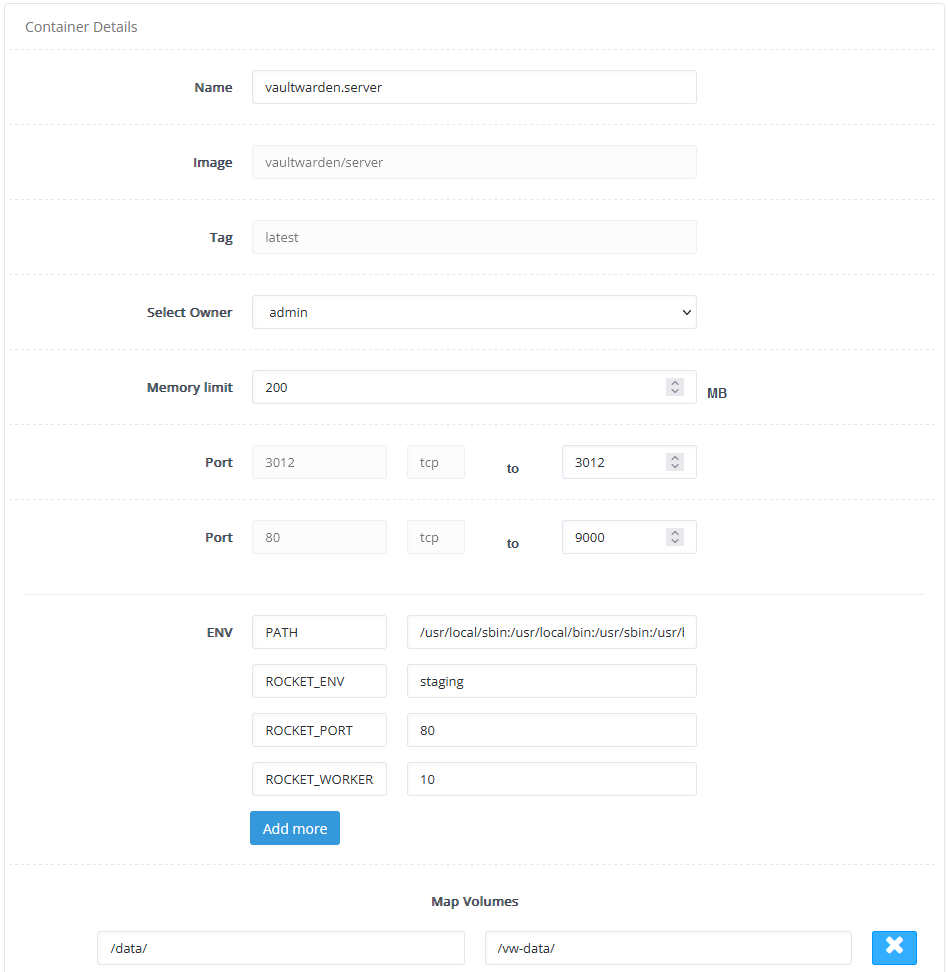
2. Container details:
3. Create token
openssl rand -base64 48
4. Add environment variables
ADMIN_TOKEN=random_token
WEBSOCKET_ENABLED=true
SIGNUPS_ALLOWED=false
5. Forward ports in OpenLiteSpeed.
-
OLS →
Virtual Hosts→Context -
Type
Static -
Enable HSTS by setting Header Operations:
Header always set Strict-Transport-Security "max-age=31536000"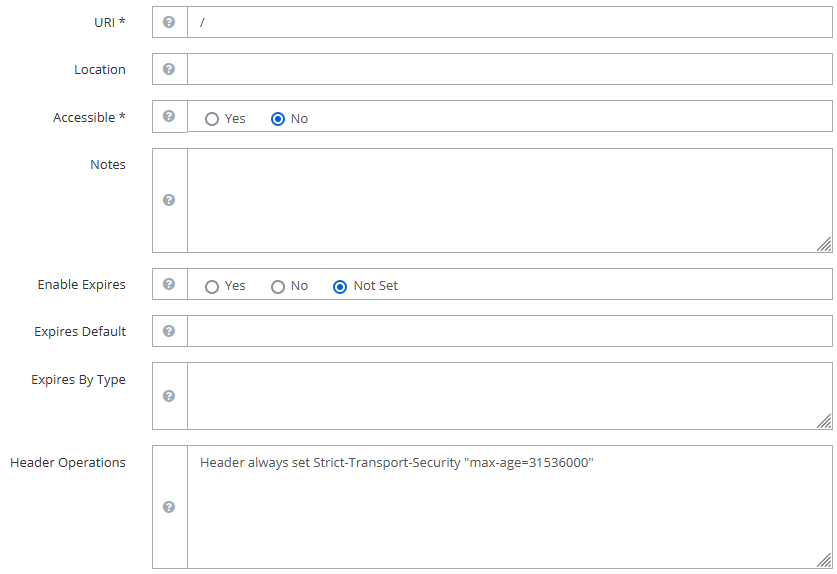
-
Rewrite Rules to redirect HTTP to HTTPS, and to the application:
RewriteEngine On RewriteCond %{HTTPS} !=on RewriteRule ^ https://%{HTTP_HOST}%{REQUEST_URI} [L,R=301] RewriteRule (.*)$ http://vaultwarden/$1 [P,L,E=PROXY-HOST:www.website.com]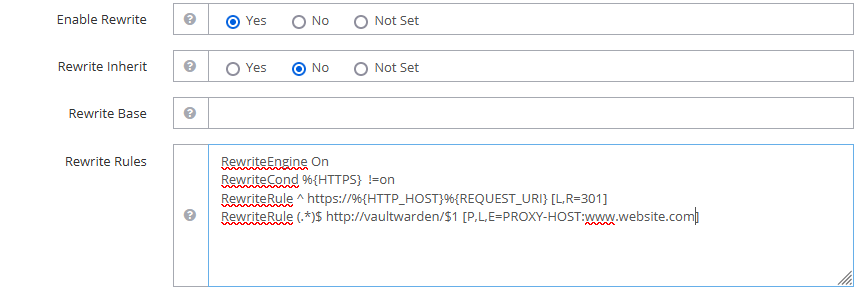
6. Docker notes:
Docker allows external access to opened ports by default. However, this is not required since we’re using a reverse proxy to direct traffic to the docker containers.
-
First method:
To prevent all traffic from external hosts to all containers, we use can use the following iptables rule (ref):
iptables -I DOCKER-USER -i eth0 -m conntrack --ctdir ORIGINAL -j DROPTo get this to start automatically, add the following in
/etc/rc.local:iptables -N DOCKER-USER iptables -I DOCKER-USER -i eth0 -m conntrack --ctdir ORIGINAL -j DROPTo specify a particular exposed port to be blocked (ref),
iptables -I DOCKER-USER -i eth0 -m conntrack --ctdir ORIGINAL --ctorigdstport 9000 -j DROP iptables -I DOCKER-USER -i eth0 -m conntrack --ctdir ORIGINAL --ctorigdstport 3012 -j DROPThis will block external access to ports 9000 and 3012.
-
Another way:
Edit or create
/etc/docker/daemon.jsonand add:{ "iptables": false }Add the following to
/etc/csf/csfpost.sh(if CSF is installed), or in/etc/rc.local(ref):#!/bin/sh echo "[DOCKER] Setting up FW rules." iptables -N DOCKER # Masquerade outbound connections from containers iptables -t nat -A POSTROUTING -s 172.17.0.0/16 ! -o docker0 -j MASQUERADE # Accept established connections to the docker containers iptables -t filter -A FORWARD -o docker0 -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT # Allow docker containers to communicate with themselves & outside world iptables -t filter -A FORWARD -i docker0 ! -o docker0 -j ACCEPT iptables -t filter -A FORWARD -i docker0 -o docker0 -j ACCEPT echo "[DOCKER] Done."Make the file executable:
chmod +x /etc/csf/csfpost.shIf CSF is installed, also add the internal IP (e.g. 172.17.0.0/16) to
/etc/csf/csf.allow.
7. Use subdirectory
To use a subdirectory e.g. domain.com/bitwarden,
- Add
External Appfor main app:- Name:
bitwarden - Address:
localhost:9000
- Name:
- Add
External Appfor notifications:- Name:
bitwardenws - Address:
localhost:3012
- Name:
- Add
StaticContext:- URI:
/bitwarden/ - Rewrite Base:
/bitwarden/ - Rewrite Rules:
RewriteRule (.*)$ http://bitwarden/bitwarden/$1 [P,L,E=PROXY-HOST:domain.com]
- URI:
- Add
StaticContext:- URI:
/bitwarden/notifications/hub/negotiate/ - Rewrite Rules:
RewriteRule (.*)$ http://bitwarden/bitwarden/$1 [P,L,E=PROXY-HOST:domain.com]
- URI:
- Add
StaticContext:- URI:
/bitwarden/notifications/hub/ - Rewrite Rules:
RewriteRule (.*)$ http://bitwardenws/$1 [P,L,E=PROXY-HOST:domain.com]
- URI:
- Add
Web Socket Proxy:- URI: `/bitwarden/notifications/hub/’
- Address:
localhost:3012